Cyber Risk Assessments: Getting your Responses to ‘Yes’
More risk for cyber insurance carriers means rates are going up and your cybersecurity stance will be tested.
Cyberattack-driven losses are on the rise, and with more businesses opting for coverage and a shrinking supply, cyber insurers are minimizing risk and demanding more from you, the policyholder. 2021 has brought higher premiums (up 32%), more coverage exclusions, and more complex risk assessments. Understanding these assessments and positioning your business to answer their questions could determine whether you can offset the costs of a cyberattack. In most cases, however, cyber insurance is necessary simply to do business and maintain contracts between existing and future business relationships
Atomic Data’s CEO Jim Wolford and CLO Mark Abbott have seen the dramatic shift in the cyber insurance industry firsthand and identified a need to consult clients in navigating their insurance risk assessments. Watch the video below to see a deeper dive into the types of questions these assessments are asking and the IT policy and process change you need to implement to get your responses to ‘yes’.
Five key questions being asked in 2022 by cyber risk insurance carriers are:
- Do you have a security program in place?
- How does your security posture look to an outsider?
- Do you give your staff the right tools to not be an inside risk?
- When an incident does happen, do you have a tested recovery plan?
- How have you handled recent public vulnerabilities?
Questions like these, once rare to see, are now commonplace for both small and medium-sized businesses. Insurers want to know the risks of coverage and will determine who qualifies by examining what policies, procedures, and security protocols exist within each company. It’s not uncommon for insurers to even run network tests against their policyholders or require that they participate in independent scoring audits.
It used to be that if a client filled out the questionnaire incorrectly, they could work with the insurer to conduct an audit and fill in the gaps. Today however, an incomplete or incorrect form could mean a significant premium increase or being dropped altogether. One client did just that and answered their assessment incorrectly, incurring a 75,000-dollar premium increase. At the end of the day, carriers do not want to underwrite the risk.
Know where you stand
Insurers want to know the ins and outs of your security program, so you’ll need to know where you stand. They’ll take a deep dive into your network and ask if you have a written information security program (WISP), effective patch management, a backup and disaster recovery strategy, firewall deployments, endpoint protection, email security, data encryption, multi-factor authentication, security policies, processes, procedures, information security training, phishing awareness, background checks, and more
Atomic Data offers risk assessment consulting services to help clients answer cyber insurance questionnaires both thoroughly and honestly. Most people can’t answer ‘yes’ to every question, but knowing where you stand and having a plan to answer ‘yes’ will give you the advantage. That’s why Atomic Data also provides IT Security as a Service. When you don’t have the proper IT solutions in place, our experts will step in and provide the in-depth discovery and gap analysis necessary to start implementing solutions and improve your IT hygiene.
Know where your data is
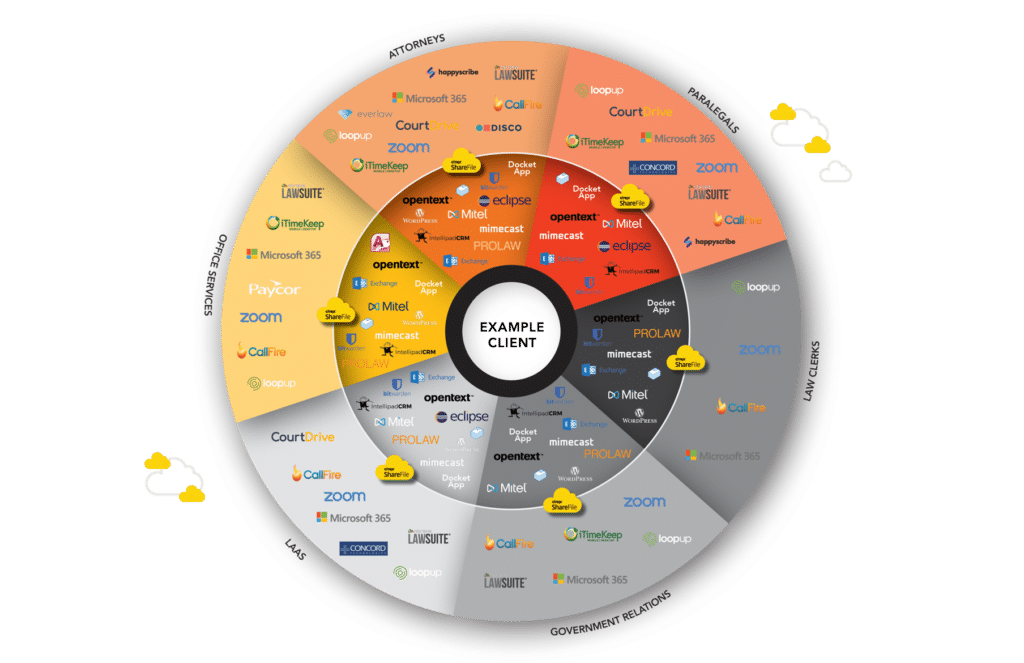
Risk assessments are no longer limited in scope to systems you control. With most businesses using cloud and Software as a Service tools, insurers are now including third parties as a part of your overall risk profile. Carriers want to make sure that you’re assessing your vendors and that they have an effective security program in place to protect your data. But before you can develop a proper vendor risk assessment policy, you need to truly understand who has access to your data. With the exploding usage of outside systems, the answer can sometimes be overwhelming. The below Data Map gives you an idea of the dozens of systems a 100+ person law firm uses in their daily operations.
The Atomic Data Map is designed to give businesses a high-level understanding of the tools their teams are using and which vendors have access to your data. In the age of ransomware as a service, insurers want to know that you can identify, track, and secure your users’ third-party application data. If you can’t, you’re at greater risk of a breach and your premiums will reflect that.
Address publicly disclosed vulnerabilities
In January of 2021, cyber attackers gained access to users’ emails, passwords, and administrative privileges on Microsoft Exchange servers worldwide. By March of 2021, at least 30,000 businesses across the US had been affected. How would you know you were impacted and what did you do to address this vulnerability? Cyber insurance questionnaires are now looking at publicly disclosed vulnerabilities and asking these types of questions. In the Exchange example, they want to know if you used an official tool to look for indicators of compromise and applied necessary patches to remediate such vulnerabilities. In this way, maintaining a pulse on public vulnerabilities and responding to them promptly will greatly enhance your security posture and minimize your coverage exclusions or rate increases.
Start with the basics
Cyberattacks, ransomware, and data loss are not a matter of if, but when. By investing time into developing proper cybersecurity programs and governance, you will save money and prevent incident-driven loss. Even more so, you’ll be better preparing your organization to handle incidents and get back up and running more quickly. Improving security posture takes time and should be done strategically. If you’re unsure about where to begin, then start with the basics! Consider drafting your own Information Security Schedule, which will serve as a starting point for a host of other critical policies like passwords, mobile devices, vendor assessments, and more.